To enforce the authentication process and guarantee that access with a specific account has actually been performed by the associated phisical person, it is possible to activate one or more of the following techniques/factors to be added to the traditional authentication method via username and password.
Email One-Time Password #
This method is based on sending a 6-digit numeric code to the email address of the user who is logging in to eurysco. The generated code will be valid for 120 seconds, can be used only once and the email message will contain a reference ID to uniquely identify the OTP code if the user has made multiple requests in a short time. This method requires that the user’s email field is filled in and SMTP settings are correctly configured.
-
-
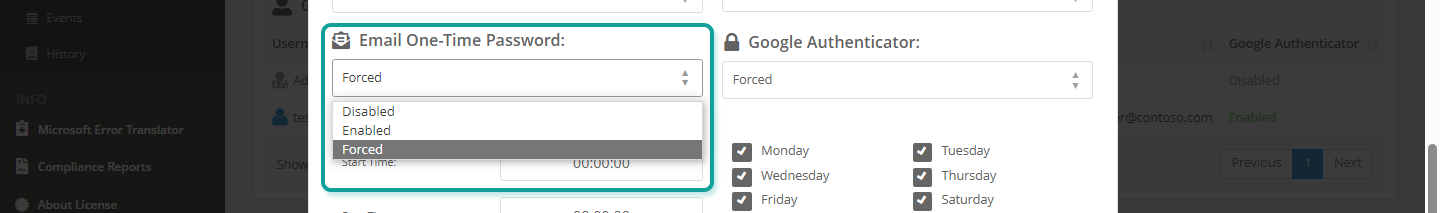
Email OTP Setting #
Select one of the following settings to disable, enable, or force OTP email when authenticating member users:
- Disabled: Function deactivated (default).
- Enabled: Function activated, but is automatically bypassed in case of problems sending the email.
- Forced: Function activated, but in case of problems sending the email the authentication process will not be able to continue.
-
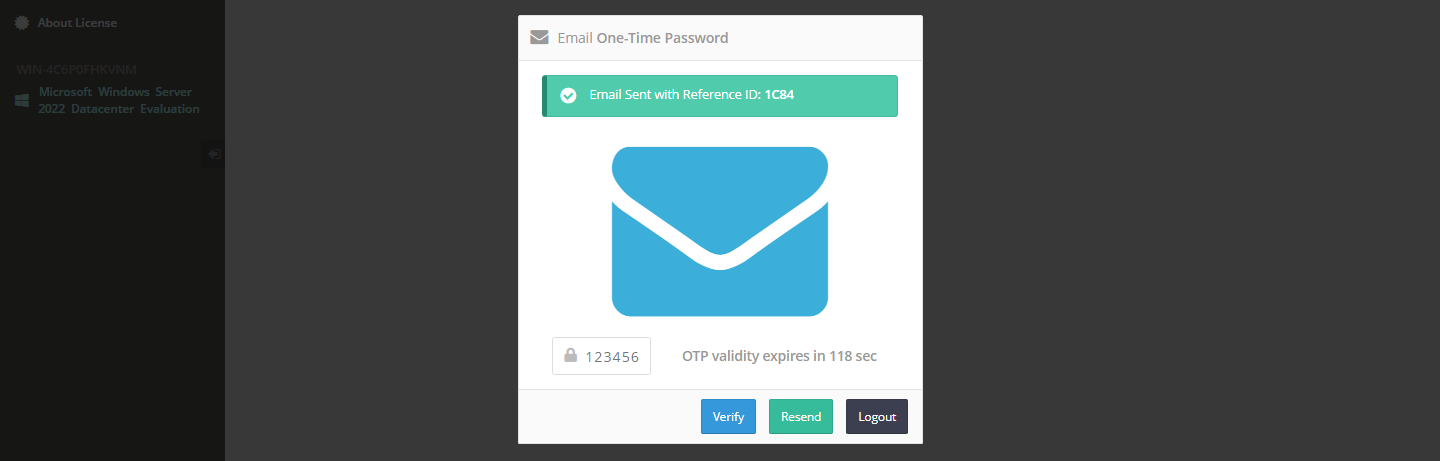
OTP email sent #
If the message is sent correctly and without errors, the popup will appear requesting the entry of the code sent via email.
-
OTP email received #
Below is an example of an OTP email received.
-
Google Authenticator #
Google Authenticator introduces an additional level of security for the authentication of Eurysco accounts, based on the use of the mobile app of the same name, it generates a 6-digit numeric code which will be requested from the user during authentication.
-
-
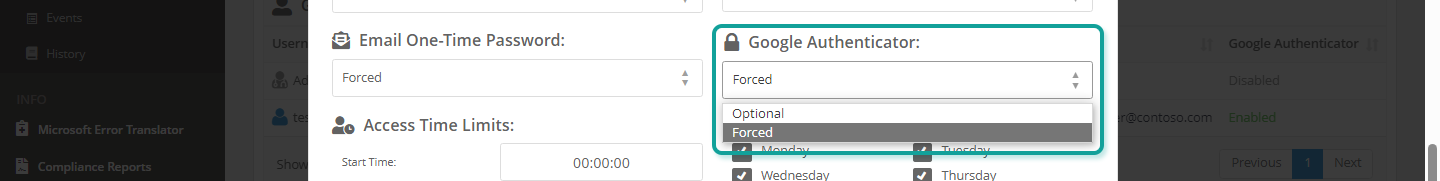
Google Authenticator Setting #
Select one of the following settings to force or not the configuration and use of the Google Authenticator app by eurysco users during login:
-
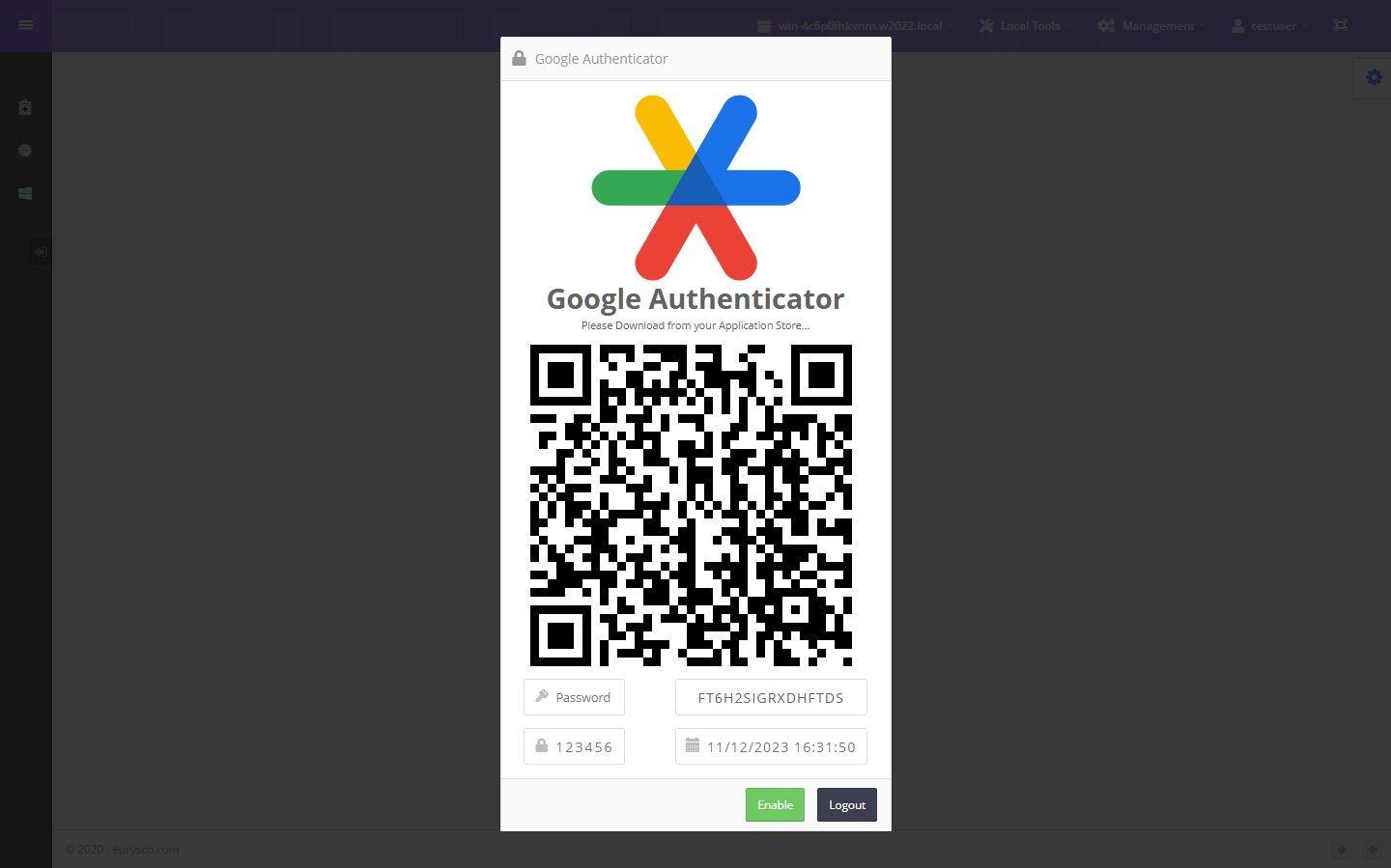
Activating Google Authenticator
#The user can conveniently configure the app via QR Code or by manually entering the alphanumeric code which must be kept by the user himself in case of restoration. Finally, to complete the configuration, simply enter the 6-digit code generated by the Google Authenticator app and the user’s password.
-
Google Authenticator Login #
After the first configuration, the user will only have to enter the 6-digit numeric code generated in the Google Authenticator app at each login.
-
Deactivating Google Authenticator #
To deactivate, simply enter the 6-digit code generated by the Google Authenticator app and the user’s password.
-
MFA User Management #
Tools and views for better MFA management of eurysco users.
-
-
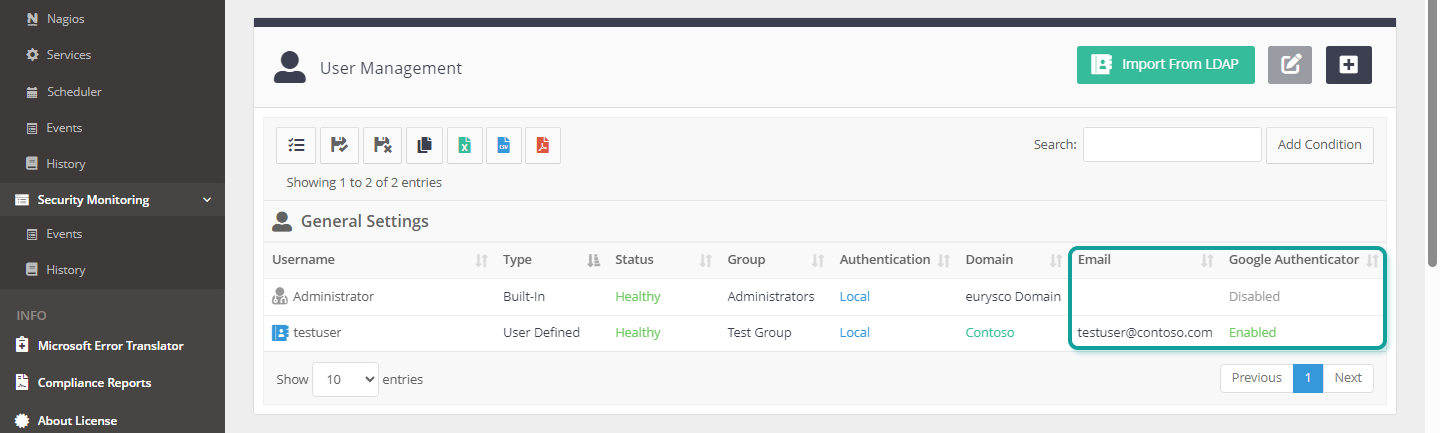
Check User Status #
Check the user configuration status from the user management console both on the completed email field necessary for receiving the OTP email and on the Google authenticator side.
-
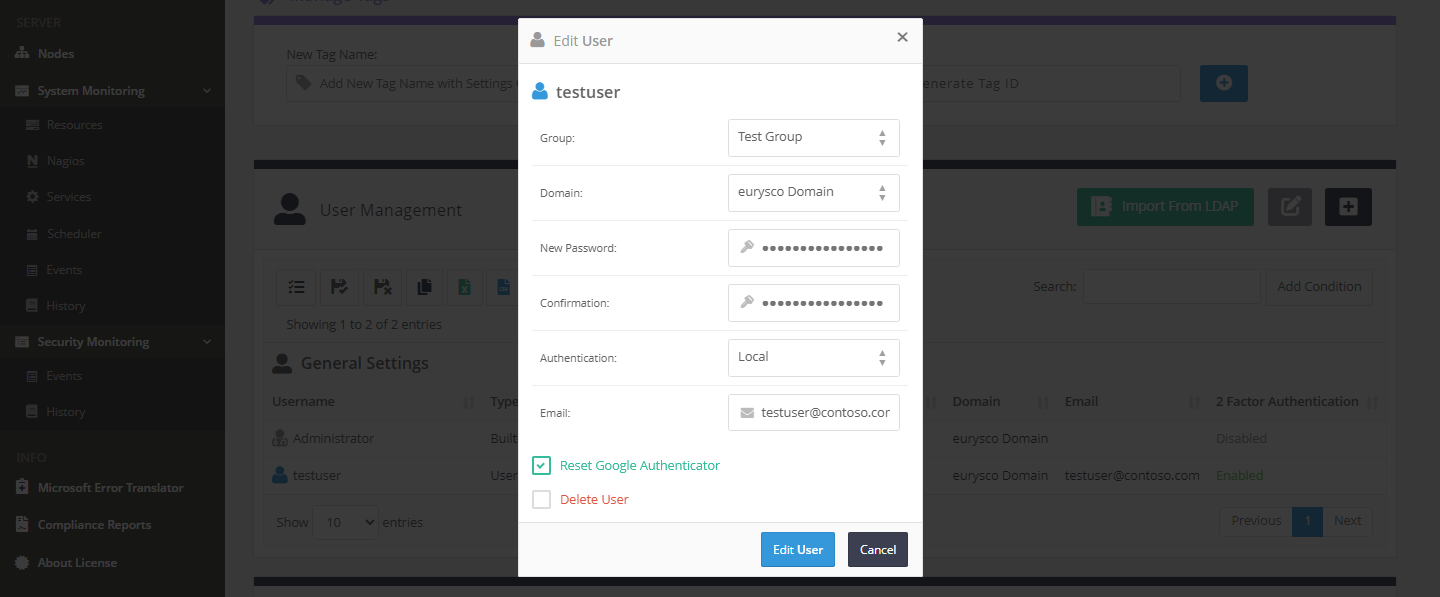
Reset Google Authenticator #
Support the user if necessary with the Google Authenticator reset which will disassociate the account from the initial code, allowing the user to deactivate the function or reconfigure it with a new code.
-